Its always bothered me that Win2003 and XP had a RRAS (Routing and Remote Access Service) that was frequently broken. Its not the same thing as ICS (Internet Connection Service). The usual failure comes after removing software or running a Registry cleaner. Then the RRAS service fails to start with error 340. Here is how to fix that.
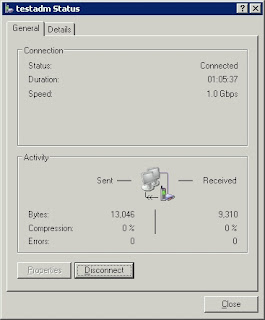
First the failure mode is (attempting to start "Routing and Remote Access") from the [services.msc] mmc snapi, the service briefly starts then stops and throws a dialog referring to Service specific error 340
The [System] Event log records:
If you enable "tracing" you can get a more detailed break down by the service, its helpers and it dependent services.
Enabling logs for RRAS - essentially a netsh command to "enable/disable" causes the logs to "appear" in the C:\WINDOWS\tracing directory.
“netsh ras set tracing * enabled”
“netsh ras set tracing * disabled”
Then when you try to start the "routing and remote access service" again, it will create new log files with more details as to status and why certain things fail (in detail). Fail and Detail, seem like a Yin and Yang don't they?
The logs are in plain text and easily readable if somewhat undocumented.
In general however they refer to services and dependent services, their calls (successful or not) and somewhat verbosely why they succeed, or why they fail.
RRAS for example has depedencies on NetbiosGroup and the RPC service, but also the Remote Access Connection Manager.. and more importantly the IAS authentication database.
All of these have more familar names and achieved their wild and wacky names through history and marketing strategy to avoid tripping over possible legal issues. Or simply to "sound" unique and different while implementing common everyday protocols used across the Internet. Balmy "Peanut butter SOAP" sounds better than simply lard butter bar.
For me IAS on XP is usually the problem.
IAS is not the "full daemon" service it is on Windows 2003 Server, its a stripped down ODBC jet engine backed microsoft access database file in the C:\Windows\system32\IAS directory which holds a few tables. It takes the place of a general purpose RADIUS authentication daemon and backend and can interface with the local accounts to validate and authorize incoming users making connection attempts. Like all file based databases its vulberable to attack and damage by "outside" forces lurking on the hard disk and in the greater operating system. Occasionally it needs to be restored or "reset" back to pristine condition from a copy of the original .mdb files that come with the WindowsXP installer on the cdrom.
MMC snapins for Windows2000 worked to manage the RRAS service on XP up through XP SP2 but after SP3 stopped working, so your reduced to using netshell or netsh commands, or third party tools to manage a "Remote Access Concentrator" or as XP calls it the "Routing and Remote Access Service". An mmc snapin is available for Win2003 but will not work on XP even if it copied over to an XP system. XPLite is a tool from Australia which appears to be able to disable the Windows File Protection system so that you can remove and reinstall RRAS.. but takes a lot of work, intuition and luck.. and does not address "missing" or corrupt registry keys.. or unregistered DLLs due to indirect software withdrawls from the system.
So first IAS may need to have its C:\WINDOWS\system32\ias default dnary.mdb and ias.mdb files restored from the Windows XP install media.. use the
Expand tool basically to unzip them and replace them, carefully moving the suspect corrupt ones to a safe backup location.
Next "missing registry keys and values"
This has been posted in many places on the internet, but I put this in a
Fixme.reg file and saved it, dbl clicked on it and merged it into the existing registry (mostly its about fixing IAS 'record store' support for RRAS):
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{6BC096C4-0CE6-11D1-BAAE-00C04FC2E20D}]
"AppID"="{A5CEB593-CCC3-486B-AB91-9C5C5ED4C9E1}"
@="IAS OLE-DB Data Store"
[HKEY_CLASSES_ROOT\CLSID\{6BC096C4-0CE6-11D1-BAAE-00C04FC2E20D}\InprocServer32]
"ThreadingModel"="Free"
@="C:\\WINDOWS\\System32\\iasrecst.dll"
[HKEY_CLASSES_ROOT\CLSID\{6BC09693-0CE6-11D1-BAAE-00C04FC2E20D}]
"AppID"="{A5CEB593-CCC3-486B-AB91-9C5C5ED4C9E1}"
@="IAS Netsh Jet Helper"
[HKEY_CLASSES_ROOT\CLSID\{6BC09693-0CE6-11D1-BAAE-00C04FC2E20D}\InprocServer32]
"ThreadingModel"="Free"
@="C:\\WINDOWS\\System32\\iasrecst.dll"
[HKEY_CLASSES_ROOT\CLSID\{6BC09692-0CE6-11D1-BAAE-00C04FC2E20D}]
"AppID"="{A5CEB593-CCC3-486B-AB91-9C5C5ED4C9E1}"
@="IAS Attribute Dictionary"
[HKEY_CLASSES_ROOT\CLSID\{6BC09692-0CE6-11D1-BAAE-00C04FC2E20D}\InprocServer32]
"ThreadingModel"="Free"
@="C:\\WINDOWS\\System32\\iasrecst.dll"
Very Important!
You then need to "re-register" a DLL which may have become unbound by some other software removal, which is referenced in the REG patch above. (as far as I can tell its the SQLquery tool that RRAS needs to get at the records in the database tables in the .mdb files)
regsvr32 C:\WINDOWS\System32\iasrecst.dll
Not done Yet!
The registry branch for the
HKLM\System\ControlSet001\Services\RemoteAccess
I put a copy of mine at the bottom of this blog post.
After the above, and a reboot for good measure.
You can RT Click [My Network Places] > Properties
Then DB Click [New Connection Wizard]
Get a list of available Inbound Connectors, Ethernet Cards, Modems Ect..
Choose whether to Modify the Firewall to allow VPN connections (I think its IPSEC)
Pick existing Windows user accounts to Auth Incoming Connection Attempts, or create new ones
Pick a networking stack over which to conduct the Auth exchange
And complete the RRAS connection type
The new type shows up in RT Click > Properties for [Network Connections]
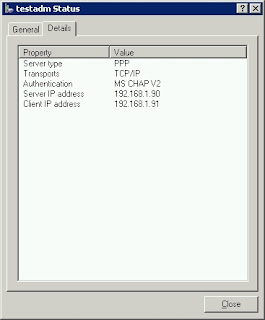
The Properties of the New Connection type reveal its configuration settings
May need to be reset to a known condition, this is mine (its more or less an out of the box example):
You
need to backup your existing registry branch (for RemoteAccess) or
perform a system restore "point" (or backup) in case this doesn't work
for you and you want to back out the changes.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess]
"Type"=dword:00000020
"Start"=dword:00000003
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,\
74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,73,\
00,76,00,63,00,68,00,6f,00,73,00,74,00,2e,00,65,00,78,00,65,00,20,00,2d,00,\
6b,00,20,00,6e,00,65,00,74,00,73,00,76,00,63,00,73,00,00,00
"DisplayName"="Routing and Remote Access"
"DependOnService"=hex(7):52,00,70,00,63,00,53,00,53,00,00,00,00,00
"DependOnGroup"=hex(7):4e,00,65,00,74,00,42,00,49,00,4f,00,53,00,47,00,72,00,\
6f,00,75,00,70,00,00,00,00,00
"ObjectName"="LocalSystem"
"Description"="Offers routing services to businesses in local area and wide area network environments."
@=""
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Accounting]
"AccountSessionIdStart"=dword:00000003
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Accounting\Providers]
"ActiveProvider"="{1AA7F846-C7F5-11D0-A376-00C04FC9DA04}"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Accounting\Providers\{1AA7F840-C7F5-11D0-A376-00C04FC9DA04}]
"ConfigClsid"="{1AA7F840-C7F5-11D0-A376-00C04FC9DA04}"
"DisplayName"="RADIUS Accounting"
"Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,72,00,\
61,00,73,00,72,00,61,00,64,00,2e,00,64,00,6c,00,6c,00,00,00
"ProviderTypeGUID"="{76560D80-2BFD-11d2-9539-3078302C2030}"
"VendorName"="Microsoft"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Accounting\Providers\{1AA7F846-C7F5-11D0-A376-00C04FC9DA04}]
"ConfigClsid"=""
"DisplayName"="Windows Accounting"
"Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,6d,00,\
70,00,72,00,64,00,64,00,6d,00,2e,00,64,00,6c,00,6c,00,00,00
"ProviderTypeGUID"="{76560D81-2BFD-11d2-9539-3078302C2030}"
"VendorName"="Microsoft"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Authentication]
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Authentication\Providers]
"ActiveProvider"="{1AA7F841-C7F5-11D0-A376-00C04FC9DA04}"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Authentication\Providers\{1AA7F83F-C7F5-11D0-A376-00C04FC9DA04}]
"ConfigClsid"="{1AA7F83F-C7F5-11D0-A376-00C04FC9DA04}"
"DisplayName"="RADIUS Authentication"
"Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,72,00,\
61,00,73,00,72,00,61,00,64,00,2e,00,64,00,6c,00,6c,00,00,00
"VendorName"="Microsoft"
"ProviderTypeGUID"="{76560D00-2BFD-11d2-9539-3078302C2030}"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Authentication\Providers\{1AA7F841-C7F5-11D0-A376-00C04FC9DA04}]
"ConfigClsid"=""
"DisplayName"="Windows Authentication"
"Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,6d,00,\
70,00,72,00,64,00,64,00,6d,00,2e,00,64,00,6c,00,6c,00,00,00
"VendorName"="Microsoft"
"ProviderTypeGUID"="{76560D01-2BFD-11d2-9539-3078302C2030}"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\DemandDialManager]
"DllPath"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,\
74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,6d,\
00,70,00,72,00,64,00,64,00,6d,00,2e,00,64,00,6c,00,6c,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces]
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\0]
"InterfaceName"="Loopback"
"Type"=dword:00000005
"Enabled"=dword:00000001
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\0\Ip]
"ProtocolId"=dword:00000021
"InterfaceInfo"=hex:01,00,00,00,68,00,00,00,03,00,00,00,05,00,ff,ff,38,00,00,\
00,00,00,00,00,40,00,00,00,04,00,ff,ff,04,00,00,00,01,00,00,00,40,00,00,00,\
07,00,ff,ff,10,00,00,00,01,00,00,00,48,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,58,02,c2,01,08,07,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\1]
"InterfaceName"="Internal"
"Type"=dword:00000004
"Enabled"=dword:00000001
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\1\Ip]
"ProtocolId"=dword:00000021
"InterfaceInfo"=hex:01,00,00,00,68,00,00,00,03,00,00,00,05,00,ff,ff,38,00,00,\
00,00,00,00,00,40,00,00,00,04,00,ff,ff,04,00,00,00,01,00,00,00,40,00,00,00,\
07,00,ff,ff,10,00,00,00,01,00,00,00,48,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,58,02,c2,01,08,07,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\2]
"InterfaceName"="{27A054EB-CD1B-4B1F-9155-4870F6D2F7F0}"
"Type"=dword:00000003
"Enabled"=dword:00000001
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\2\Ip]
"ProtocolId"=dword:00000021
"InterfaceInfo"=hex:01,00,00,00,68,00,00,00,03,00,00,00,05,00,ff,ff,38,00,00,\
00,00,00,00,00,40,00,00,00,04,00,ff,ff,04,00,00,00,01,00,00,00,40,00,00,00,\
07,00,ff,ff,10,00,00,00,01,00,00,00,48,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,58,02,c2,01,08,07,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\3]
"InterfaceName"="{2997EDE8-4DF4-4409-BF1D-E35E6F580C2F}"
"Type"=dword:00000003
"Enabled"=dword:00000001
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Interfaces\3\Ip]
"ProtocolId"=dword:00000021
"InterfaceInfo"=hex:01,00,00,00,68,00,00,00,03,00,00,00,05,00,ff,ff,38,00,00,\
00,00,00,00,00,40,00,00,00,04,00,ff,ff,04,00,00,00,01,00,00,00,40,00,00,00,\
07,00,ff,ff,10,00,00,00,01,00,00,00,48,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,58,02,c2,01,08,07,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters]
"RouterType"=dword:00000001
"ServerFlags"=dword:00802702
"ServiceDll"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,\
00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,\
6d,00,70,00,72,00,64,00,69,00,6d,00,2e,00,64,00,6c,00,6c,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\AccountLockout]
"MaxDenials"=dword:00000000
"ResetTime (mins)"=dword:00000b40
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\AppleTalk]
"EnableIn"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\Ip]
"AllowClientIpAddresses"=dword:00000000
"AllowNetworkAccess"=dword:00000001
"EnableIn"=dword:00000001
"IpAddress"="0.0.0.0"
"IpMask"="0.0.0.0"
"UseDhcpAddressing"=dword:00000001
"EnableNetbtBcastFwd"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\Ip\StaticAddressPool]
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\Ip\StaticAddressPool\0]
"From"=dword:00000000
"To"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\Ipx]
"EnableIn"=dword:00000001
"AcceptRemoteNodeNumber"=dword:00000001
"AllowNetworkAccess"=dword:00000001
"AutoWanNetAllocation"=dword:00000001
"FirstWanNet"=dword:00000000
"GlobalWanNet"=dword:00000001
"LastWanNet"=dword:00000000
"WanNetPoolSize"=dword:000003e8
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Parameters\Nbf]
"EnableIn"=dword:00000001
"AllowNetworkAccess"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Performance]
"Open"="OpenRasPerformanceData"
"Close"="CloseRasPerformanceData"
"Collect"="CollectRasPerformanceData"
"Library"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,\
74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,72,\
00,61,00,73,00,63,00,74,00,72,00,73,00,2e,00,64,00,6c,00,6c,00,00,00
"First Counter"=dword:000007de
"First Help"=dword:000007df
"Last Help"=dword:00000805
"Last Counter"=dword:00000804
"WbemAdapFileSignature"=hex:b0,b0,d7,90,5a,c7,1b,c2,78,f1,7f,45,5e,18,26,11
"WbemAdapFileTime"=hex:00,a0,a1,10,27,9e,c8,01
"WbemAdapFileSize"=dword:00002e00
"WbemAdapStatus"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy]
"ProductDir"="C:\\WINDOWS\\system32\\IAS"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline]
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\01]
@="IAS.ProxyPolicyEnforcer"
"Requests"="0 1 2"
"Responses"="0 1 2 3 4"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\02]
@="IAS.NTSamNames"
"Providers"="1"
"Requests"="0"
"Responses"="0 1 3"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\03]
@="IAS.BaseCampHost"
"Requests"="0 1"
"Responses"="0 1 2 4"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\04]
@="IAS.RadiusProxy"
"Providers"="2"
"Responses"="0"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\05]
@="IAS.NTSamAuthentication"
"Providers"="1"
"Requests"="0"
"Responses"="0"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\06]
@="IAS.AccountValidation"
"Providers"="1"
"Requests"="0"
"Responses"="0 1"
"Reasons"="33"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\07]
@="IAS.PolicyEnforcer"
"Providers"="1"
"Requests"="0"
"Responses"="0 1 3"
"Reasons"="33"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\08]
@="IAS.NTSamPerUser"
"Providers"="1"
"Requests"="0"
"Responses"="0 1 3"
"Reasons"="33"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\09]
@="IAS.EAP"
"Providers"="1"
"Requests"="0 2"
"Responses"="0"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\10]
@="IAS.URHandler"
"Providers"="0 1"
"Requests"="0 2"
"Responses"="0 1"
"Reasons"="33"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\11]
@="IAS.ChangePassword"
"Providers"="1"
"Requests"="0"
"Responses"="0 1"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\12]
@="IAS.AuthorizationHost"
"Requests"="0 1 2"
"Responses"="0 1 2 4"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\13]
@="IAS.Accounting"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Policy\Pipeline\14]
@="IAS.MSChapErrorReporter"
"Providers"="0 1"
"Requests"="0"
"Responses"="2"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\RouterManagers]
"Stamp"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\RouterManagers\Ip]
"ProtocolId"=dword:00000021
"GlobalInfo"=hex:01,00,00,00,80,00,00,00,02,00,00,00,03,00,ff,ff,08,00,00,00,\
01,00,00,00,30,00,00,00,06,00,ff,ff,3c,00,00,00,01,00,00,00,38,00,00,00,00,\
00,00,00,00,00,00,00,01,00,00,00,07,00,00,00,02,00,00,00,01,00,00,00,03,00,\
00,00,0a,00,00,00,16,27,00,00,03,00,00,00,17,27,00,00,05,00,00,00,12,27,00,\
00,07,00,00,00,0d,00,00,00,6e,00,00,00,08,00,00,00,78,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00
"DLLPath"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,\
74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,69,\
00,70,00,72,00,74,00,72,00,6d,00,67,00,72,00,2e,00,64,00,6c,00,6c,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\RoutingTableManager]
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\RoutingTableManager\Instance 00000]
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\RoutingTableManager\Instance 00000\AddressFamily 00002]
"AddressSize"=dword:00000004
"ViewsSupported"=dword:00000003
"MaxChangeNotifyRegistrations"=dword:00000010
"MaxOpaqueInfoPointers"=dword:00000005
"MaxNextHopsInRoute"=dword:00000003
"MaxHandlesReturnedInEnum"=dword:00000019
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,00,01,00,00,\
00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,00,01,01,00,00,00,00,00,\
05,12,00,00,00,00,00,18,00,ff,01,0f,00,01,02,00,00,00,00,00,05,20,00,00,00,\
20,02,00,00,00,00,14,00,8d,01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,\
00,18,00,fd,01,02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,\
00,00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RemoteAccess\Enum]
"0"="Root\\LEGACY_REMOTEACCESS\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001